The Valet Key Pattern: A Comprehensive Guide to Controlled Access
Introduction
In the complex landscape of cloud computing, controlling access to data stores is a multifaceted challenge. Traditional authentication and authorization mechanisms may fall short, especially when the data store itself can't manage these aspects. Enter the Valet Key Pattern, a solution that elegantly addresses this issue by providing controlled, time-limited access to specific resources.
What is the Valet Key Pattern?
The Valet Key Pattern is a security design pattern that involves generating a temporary key or token, referred to as a valet key. This key grants limited access to specific resources, allowing predefined operations such as reading, writing, uploading, or downloading.
Key Characteristics
-
Time-Limited: The key is valid for a specific period, after which it becomes invalid.
-
Scope-Specific: The key can specify access to particular tables, rows, containers, or items.
-
Predefined Operations: The key allows only certain actions, such as reading or writing.
How the Valet Key Pattern Works
1. Generating the Key
The application creates a valet key with specific attributes:
-
Access Permissions: Defines what actions the client can perform.
-
Time Validity: Sets how long the key is valid.
-
Scope of Data: Specifies the data's location and extent that the key can access.
2. Client Usage
The client uses the key to access the specified resource in the data store, adhering to the restrictions set by the key.
3. Key Expiration and Invalidation
The key automatically becomes invalid after the specified period or can be manually invalidated by the application.
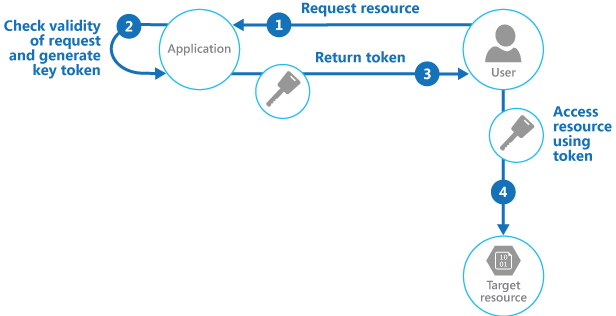
Image credits to microsoft
Practical Applications
-
File Uploads and Downloads: Allow clients to upload or download files without giving them direct access to the storage account.
-
Temporary Access to Data: Grant temporary access to specific data, such as a shared document or database.
-
Third-Party Integrations: Enable third-party services to perform actions without exposing full credentials.
Implementing the Valet Key Pattern: A Java Example
Let's explore a practical example of implementing the Valet Key Pattern for file uploads in a cloud storage system.
Step 1: Client Requests Access
The client requests access to upload a file. The server validates the request.
public Token requestUploadAccess(String clientId) {
// Validate client
// ...
return generateUploadToken(clientId);
}
Step 2: Server Generates Token
The server generates a token with specific permissions and a time limit.
private Token generateUploadToken(String clientId) {
// Define permissions and time limit
// ...
return new Token(permissions, expirationTime);
}
Step 3: Client Uploads File
The client uses the token to upload the file to the specified location.
public void uploadFile(Token token, File file) {
// Validate token
// ...
// Upload file
// ...
}
Step 4: Token Expiration
The token automatically expires after the specified time, or the server can invalidate it.
public void invalidateToken(Token token) {
// Invalidate token
// ...
}
Benefits of the Valet Key Pattern
-
Enhanced Security: Minimizes risk by limiting access.
-
Simplified Management: Reduces complexity in user management.
-
Improved Performance: Removes processing overhead from the application.
Considerations and Best Practices
-
Tight Control Over Validity Period: Limit the key's validity to minimize potential misuse.
-
Precise Specification of Location: Ensure that the key's recipient can only use it for the intended purpose.
-
Monitoring and Auditing: Implement monitoring to track key usage and maintain compliance.
Conclusion
The Valet Key Pattern is a versatile and robust solution for controlling access to data stores in scenarios where traditional methods may not suffice. By understanding its workings, applications, benefits, and considerations, organizations can implement this pattern to enhance security, simplify management, and optimize performance.
Whether you are a developer, architect, or security professional, the Valet Key Pattern offers a practical approach to access control that aligns with modern cloud architectures.
